How to trigger Software Updates Re-Scan in Configuration Manager 2012 SP1
How to trigger Updates Re-scan in SCCM 2012
Did you ever do a OSD in Configuration Manager and wonder why some Software Updates weren’t installed?
As a workaround, did you try adding more “Install Software Updates” steps to your Task Sequence?
It probably didn’t work, did it?
The answer to this is ‘simple’. The ConfigMgr agent caches the results of a Software Update evaluation scan in a cache and this cache seems to have a rather long TTL, at least when talking about OSD, where you usually have a “Install Software Updates” step at the beginning and at the end of the Task Sequence.
The step at the end will most likely don’t do a re-scan, because the cache is still valid.
How to trigger a re-evaluation of Software Updates?
The answer to this question has been around for some time now, as this problem was also present with ConfigMgr 2007.

It’s possible to tell the SMS Agent to forget the cache (in fact, you’re telling it that the TTL is invalid, see picture above) and do a re-evaluation of Software Updates.
There is a WMI method in the SMS Client’s namespace called “TriggerSchedule” which accepts certain ScheduleIDs. Jürgen Pietsch wrote them down here: http://social.technet.microsoft.com/Forums/en-US/configmanagerosd/thread/a535e509-fc6a-483c-bf24-7e2aa064e5b7/
Knowing the ID we can go ahead and trigger it. This can be done in several ways:
WMIC (like in the thread on technet):
WMIC /namespace:\\root\ccm path sms_client CALL TriggerSchedule "{00000000-0000-0000-0000-000000000113}" /NOINTERACTIVE
I translated it to PowerShell:
([wmiclass]‘root\ccm:SMS_Client’).TriggerSchedule(‘{00000000-0000-0000-0000-000000000113}’)
Or even via the Right-Click tools by Ryan Ephgrave (MyITForum) for the ConfigMgr console (of course, not during the OSD).
How to trigger Software Update rescan on Windows Server 2012 and Windows 8?
ConfigMgr 2012 SP1 supports Windows Server 2012 and Windows 8 (and more) and here we found the same problem as described above.
Fortunately, it still works with the new OS versions and it looks like there are a few more Triggers now with ConfigMgr 2012 SP1 compared to the versions before, although I don’t now (yet!) why there are so much doubles.
ScheduledMessageID | TargetEndPoint |
{00000000-0000-0000-0000-000000000223} | direct:ExternalEventAgent direct:EndpointProtectionAgent direct:EndpointProtectionAgent direct:pwrmgmt direct:DCMAgent direct:OOBMgmt direct:StateMessageManager direct:UpdateStore direct:ScanAgent direct:StateMessageManager direct:StateMessageManager direct:UpdatesDeploymentAgent direct:CertificateMaintenanceEndpoint direct:PolicyAgent_RequestAssignments direct:PolicyAgent_Cleanup direct:SrcUpdateMgr direct:SWMTRReportGen direct:LS_ScheduledCleanup direct:LS_ScheduledCleanup direct:LS_ScheduledCleanup direct:PolicyAgent_PolicyEvaluator direct:PolicyAgent_RequestAssignments direct:InventoryAgent direct:InventoryAgent direct:InventoryAgent direct:InventoryAgent |
The trigger 113 is still available and can be used on Windows 8 and Windows Server 2012:
After executing the trigger via the PowerShell and having a look at the client’s ‘ScanAgent.log’, we see that it succeeded: 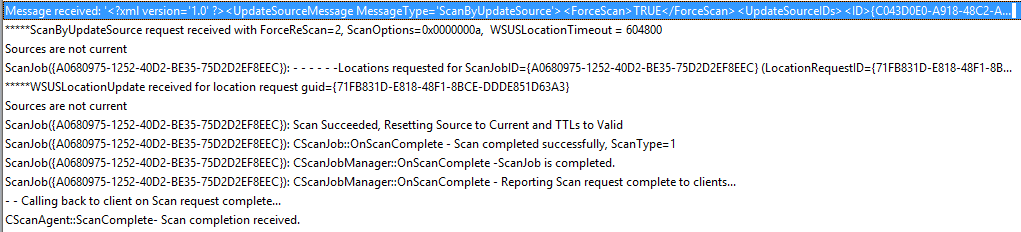
Do you use other triggers on a regular basis? If so, which and why? I’m very interested in learning more about the other triggers and how you might use them.

Leave a Comment